--
Fort Worth, TX. This McAfee Labs Threats Report found that open-source ransomware code and ransomware-as-a-service continue to make it simpler to launch attacks, and ransomware campaigns continue to be financially lucrative.
While no computers are completely impenetrable, not even the Mac, there are precautions to take to prevent losses. To prevent the hazards, it’s important to understand the causes. In a recent article, Paul Mah of CIO Magazine wrote: “Spyware, malware, phishing and, more recently, ransomware — these online threats can be confusing and daunting. Knowing the threats is half the battle. Each of these types of attacks have specific characteristics:
· Spyware – software that collects personal information from computers without permission or knowledge.
· Malware – a broad category of software (including viruses, worms, Trojan horses, etc.) that damages the computer, in either a minor or major way.
· Phishing – an attempt to get personal information (usernames, passwords, credit card numbers and), usually for nefarious reasons. Usually accomplished by electronic communication (e.g., email), but also by “social engineering” (tricking people into trusting them).
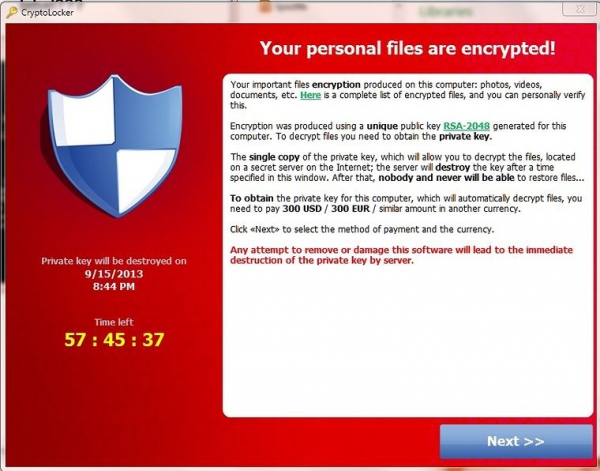
· Ransomware – a much more extreme version of spyware that will actually threaten to lock the computer or encrypt it, unless a fee or ransom is paid. Earlier this year, ransomware attacks targeted major U.S. and British publications and hospitals.”The level of technical sophistication in ransomware has gone up again from last year,” when Intel devoted its threats report to the problem.
There are ways to minimize the effects of the attack, but needs to act BEFORE an attacker strikes. It takes less than 5 minutes from the time the malware gets on a system to the time when primary files are encrypted, backup files are deleted, and the demand for ransom is presented.”
That said, here are five steps from a recent NetworkWorld.com article for surviving a ransomware, malware, trojan or virus attack:
1. Plan a response now – For most types of ransomware attacks, minutes and seconds count, so the time to plan how to respond is well before an attack happens. Experts recommend developing an incident response plan that is specific for this type of attack. The plan should detail roles, responsibilities and actions to take as soon as the organization becomes aware of an active attack.
2. Backup all data – Ransomware attacks are known for encrypting current data and also deleting backup data wherever it can be reached. It encrypts files on all drives, including external devices such as USB thumb drives, online backup services, and cloud file stores where a drive letter has been assigned. Make sure backups aren’t accessible from endpoints through disk mounts because they will be encrypted too.
3. Keep installed antivirus software current – All of the major anti-malware, anti-spyware and anti-virus software vendors are researching ransomware so they can identify and manage the continually changing threats.
4. Screen emails for phishing/malware – The 2016 Verizon Data Breach Incident Report says that email messages with malicious attachments or links are a major avenue for installation of ransomware. FireEye confirms that most ransomware is delivered via email. This makes it important to screen incoming emails and filter out what appears to be phishing messages or malicious attachments. It’s especially important to filter on executable files. Some phishing messages use deception by making executable files appear to be regular PDF files.
5. Be vigilant to avoid phishing attempts – People are gullible and trusting, and fail for social engineering tricks that persuades opening and click on the phishes. With these recent spikes in rogue activities, the best offense is also the best defense. Be cautious of email from anyone other than personal Contacts or close friends. Have a premium quality ‘real time scanning’ anti-virus program that gets updates automatically, and has a multi-faceted approach to protecting all devices.
McAfee Total Protection 2016 has a full featured protection suite that won numerous awards for being the ‘Best Value’ and is truly a Best in Class protection system for Windows PC, Mac, Android and iOS Devices. In an effort to enhance consumers’ protection levels, McAfee is offering a limited time deep discount on their Antivirus products, using digital downloads, for immediate protection. Buy with confidence as they offer a 30-Day Money Back Guarantee, 24/7 Free Support, and satisfaction is guaranteed. Buy now to prevent these malicious attacks on privacy, security and lifestyle.
Release ID: 115117

